New 2020 Survey Report on Security Practices in HPC & HPC Cloud
With the current trend of HPC workloads and infrastructure increasingly becoming cloud-like (e.g., resource pooling, rapid elasticity, on-demand self-service), or interacting with the cloud (e.g., bursting), security will become a greater concern at an accelerating rate. The secure interchange of data between traditional HPC and HPC Cloud, and the portability of a user’s HPC workflow and tools are critical elements of HPC Cloud use. Where a traditional HPC environment has a dedicated team of administrators, a HPC Cloud environment may rely on the use of community-supported, generically preconfigured tools from sources like OpenHPC (http://www.openhpc.community/).
To start working towards providing a backdrop for developing a set of best practices / guidelines to secure HPC / HPC Cloud, the Cloud Security Alliance (CSA) released survey report this week to provide insights into the level and type of cyber and cloud security adopted by HPC / HPC Cloud infrastructure to protect their infrastructure and workloads. The report, “Security Practices in HPC & HPC Cloud” is the first deliverable presented by CSA’s High Performance Computing (HPC) Cloud Security Working Group.
What are the challenges of HPC workloads becoming more cloud-like?
‘Vanilla’ Cloud environments were typically not made to handle harsh environments like that of HPC. Technical concerns for HPC are further complicated by the complex and ever-evolving threat landscape. As we increasingly see cases of pure HPC bare metal infrastructure interacting with the cloud (such as I/O interfaces and processes), it brings along more ‘opportunities’ for malicious attacks. While this should be considered and integrated into security policies and guidelines, performance faces the peril of being compromised as precious resources are carved out for security protocols and processes. The crossing of cloud and HPC environments often leads us to questions of how security in an HPC Cloud environment can be implemented, enforced and ensured without the need to compromise performance. This working group strives to provide recommendations that can answer these questions. https://cloudsecurityalliance.org/research/working-groups/high-performance-computing-cloud-security/
The report highlights common challenges faced by the HPC sector.
The survey report from CSA shines a light on common challenges faced in the industry, together with the real-world security processes put in place to tackle such hindrances. The observations presented through this report highlight learning points for the HPC sector in terms of the perceived level of security in the sector, perception of security vs performance, drivers and impediments to cloud-enablement and improving security postures, and security practices that could be adopted in HPC / HPC Cloud environments.
Key findings from the report
To start working towards providing a backdrop for developing a set of best practices / guidelines to secure HPC / HPC Cloud, the Cloud Security Alliance (CSA) released survey report this week to provide insights into the level and type of cyber and cloud security adopted by HPC / HPC Cloud infrastructure to protect their infrastructure and workloads. The report, “Security Practices in HPC & HPC Cloud” is the first deliverable presented by CSA’s High Performance Computing (HPC) Cloud Security Working Group.
What are the challenges of HPC workloads becoming more cloud-like?
‘Vanilla’ Cloud environments were typically not made to handle harsh environments like that of HPC. Technical concerns for HPC are further complicated by the complex and ever-evolving threat landscape. As we increasingly see cases of pure HPC bare metal infrastructure interacting with the cloud (such as I/O interfaces and processes), it brings along more ‘opportunities’ for malicious attacks. While this should be considered and integrated into security policies and guidelines, performance faces the peril of being compromised as precious resources are carved out for security protocols and processes. The crossing of cloud and HPC environments often leads us to questions of how security in an HPC Cloud environment can be implemented, enforced and ensured without the need to compromise performance. This working group strives to provide recommendations that can answer these questions. https://cloudsecurityalliance.org/research/working-groups/high-performance-computing-cloud-security/
The report highlights common challenges faced by the HPC sector.
The survey report from CSA shines a light on common challenges faced in the industry, together with the real-world security processes put in place to tackle such hindrances. The observations presented through this report highlight learning points for the HPC sector in terms of the perceived level of security in the sector, perception of security vs performance, drivers and impediments to cloud-enablement and improving security postures, and security practices that could be adopted in HPC / HPC Cloud environments.
Key findings from the report
- The majority of respondents (66.7%) expressed deep concerns about the risk of cyber threats to HPC infrastructure and workloads
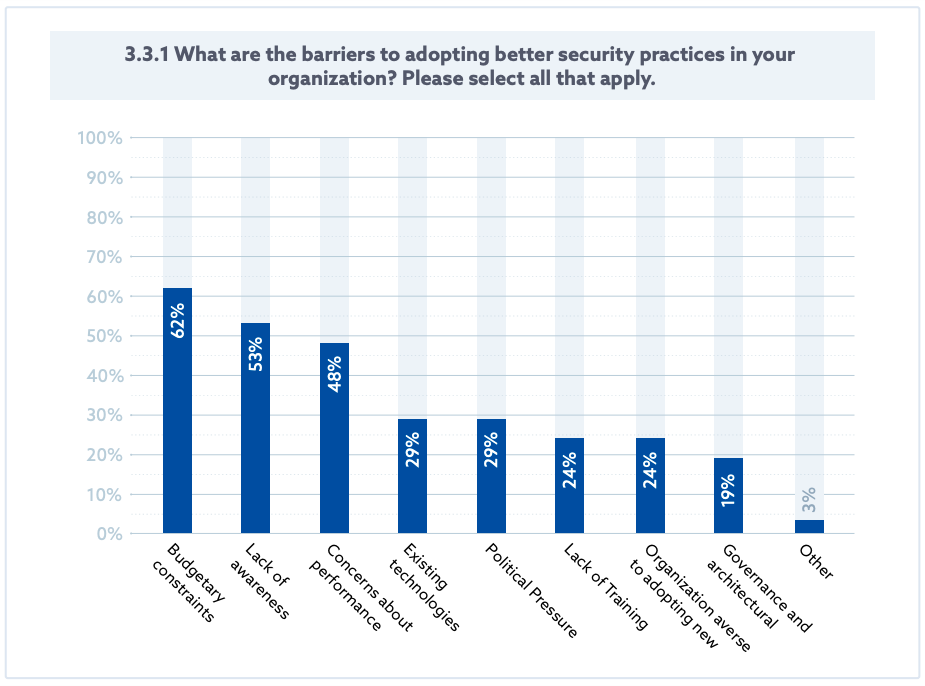
- When asked what the barriers to adopting better security practices where, the majority of respondents listed budgetary constraints and lack of awareness.
- Slightly more than 50% of respondents’ organizations do not tap industry guidelines / standards for cybersecurity.
- About half of the respondents are offering cloud-based HPC services.
- A dominating concern specific to the HPC sector impeding cloud adoption is performance tradeoff (80%). Interestingly, only 10% of respondents cited not meeting security requirements as a barrier to cloud adoption.