|
|
Welcome to the CSA APAC Cloud Codebook!
A monthly newsletter, and your source for the most up-to-date news on CSA APAC Region.
|
|
|
|
|
|
Corporate Members Spotlight
Check out what our corporate members are doing!
|
|
|
|
Standard Chartered Bank (Singapore), Singapore
Cloud Security Alliance visited Standard Chartered Bank in Singapore to discuss the top 5 trends in changing the information security. The discussion lead to focus on future virtualization where containers will gain momentum. CSA also talked about IoT as a trend and shared some best practices from IoT working group. CSA also shared that many of the bad things that happen in information security have as their root cause a lack of sharing. Sharing of the signs of a potential attack could have prevented many of the most significant breaches. Organizations are reluctant to share for privacy or legal reasons.
Our industry needs a revolution in the way we think about sharing, by adding anonymization and preventing attribution, we may be able to change the culture to a “default share” attitude. CSA is working on this with the Cloud CISC (Cyber Incident Sharing Center).
|
|
|
|
|
CSA APAC Research Activities
Check out our research activities!
|
|
|
|
Virtualization Working Group
Peer review is open for Virtualization Working Group's network virtualization security whitepaper, Security Position Paper for Network Function Virtualization. The whitepaper offers a framework for approaching network virtualization security when applied to network function virtualization (NFV). It references software-defined networking (SDN) concepts, because SDN is the critical virtualization-enabling technology. This paper speaks primarily to a technical audience but business decision makers can readily understand it.
|
|
|
|
Mobile Application Security Testing (MAST) Working Group
Mobile applications have not only become indispensable to modern life, but have also been part of all organizations. With the emergence of cloud computing technology, organizational reinforcement is needed to adapt to the massive change. Cloud computing enables real-time use of applications, by which it offers enterprise the enormous flexibility. Accompanied by the convenience; with the inclusion of applications, security problems result from the lack of transparency and present challenges to risk management.
The goal of the project strives to create a more secured cloud ecosystem to protect mobile applications. Engineering methods are established by system protection and applied to structure, design testing, and review of applications. These assist in integrations and introduce security, quality control, and compliable evidence in mobile application development and management.

|
|
|
The project wishes to conduct more research in mobile application security vetting; the efforts help organizations and individuals reduce the possible risk exposures and security threat in using mobile applications. For peer review of the MAST white paper, please contact: [email protected]
|
|
|
|
|
|
Memoir of An Analyst
Our thoughts on cloud security
|
|
|
|
Internet of Things

|
|
Recap of the previous edition
In the previous edition, the topic was centered around mobile application security testing. For example, how important mobile application security is and how can we secure the apps. In this edition, we will talk about another technology which affects our daily lives - Internet of Things.
Internet of Things
Internet of Things (IoT) has been a buzzword for many years. IoT devices such as Google and Apple Watch have been widely spread all over the consumer sector, however the business and the public sectors are lagging behind in the adoption of IoT. What caused this?
Adoption of IoT
Similar to the adoption of cloud, the adoption of IoT is strongly delayed by the security and privacy issues around the technology. While IoT connects physical ‘Things’ with virtual ‘Things’, it also creates backdoors for attackers to gain advantages over the users. Attackers can steal away your personal information such as your heart beat rate or even your life! Attackers can steal away your life just by turning on your IoT enabled heater while you are asleep without being next to you!
In fact, 6 out of 10 devices that provide user interfaces were vulnerable to a range of issues such as persistent XSS and weak credentials. 3 in 10 smart watches and their applications were vulnerable to Account Harvesting.
Why do we still want it?
So why do we still want to embrace it if IoT is such an evil tool?
IoT makes our lives “Smarter”!
From Smart TV to Smart Parking. It brings convenience to us and makes our lives much easier. We can save money by having Smart Lighting in our home, lights will be switched off automatically if there is no one around. We just need to walk into our home and the lights will be turned on for us. You can turn on your air conditioner on the way back home from work through your smartphone. Doctors are able to track their patients’ health condition remotely through the health tracking wearables. IoT benefits us in many different aspects.
Have a look at the image below and see how ‘Smart’ our lives can be with IoT technology!
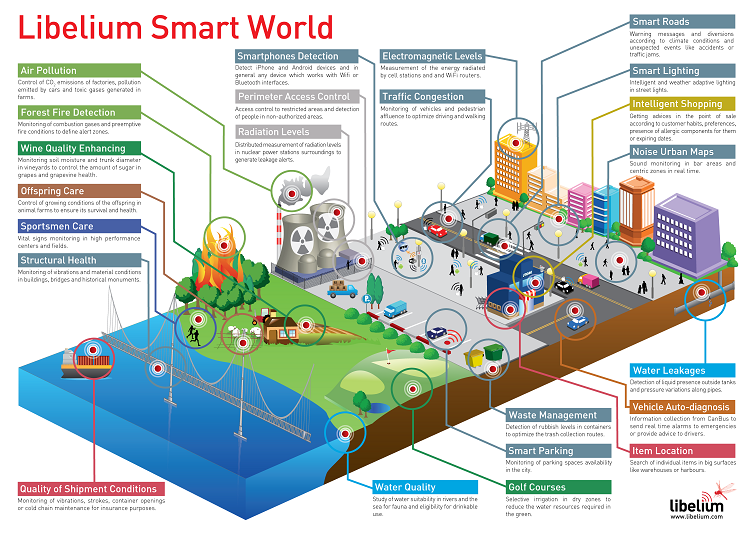 source: http://blogs-images.forbes.com/jacobmorgan/files/2014/05/libelium_smart_world_infographic_big.png
source: http://blogs-images.forbes.com/jacobmorgan/files/2014/05/libelium_smart_world_infographic_big.png
What can we do?
So how can we make our lives ‘Smarter’ without putting ourselves in risk? As IoT creates a brand new threat vector, proper security and review process should be implemented to protect the IoT consumers. Back in April 2015, CSA published our Security Guidance for Early Adopters of the IoT. In the document, we provide guidance for secure implementation of IoT-based system. As IoT introduces new security challenges such as privacy concerns and mass quantities, relying on traditional enterprise security solutions is not enough to protect the IoT adopters. Our guidance defines 7 recommended IoT security controls to address the challenges. We believe these tailored security controls are able to mitigate many of the risks associated with the IoT technology.
We hope that through providing security guidance and best practices to IoT adopters, the technology will be more applicable to the real world, and everyone will be able to enjoy the benefits of using this technology.
References & Further Reading
Cloud Security Alliance, 'Security Guidance for Early Adopters of the Internet of Things (IoT)', 2015. [Online]. Available: https://downloads.cloudsecurityalliance.org/whitepapers/Security_Guidance_for_Early_Adopters_of_the_Internet_of_Things.pdf. [Accessed: 6- Nov- 2015].
B. O’Brien, 'Why the ‘Internet of Things’ is Important', Recurring Revenue Blog | Aria Systems, 2014. [Online]. Available: https://www.ariasystems.com/blog/internet-things-important/. [Accessed: 6- Nov- 2015].
Owasp.org, 'OWASP Internet of Things Project - OWASP', 2015. [Online]. Available: https://www.owasp.org/index.php/OWASP_Internet_of_Things_Top_Ten_Project. [Accessed: 6- Nov- 2015].
Hewlett Packard Enterprise Development LP, 'HPE Fortify and the Internet of Things', 2015. [Online]. Available: http://go.saas.hp.com/fod/internet-of-things. [Accessed: 6- Nov- 2015].
Hewlett Packard Enterprise Development LP, 'Internet of Things Security Study: Smartwatches', 2015. [Online]. Available: http://go.saas.hp.com/l/28912/2015-07-20/325lbm/28912/69038/IoT_Research_Series_Smartwatches.pdf. [Accessed: 6- Nov- 2015].
Hewlett Packard Enterprise Development LP, 'Internet of Things Research Study 2014 Report'. 2015. [Online]. Available: http://go.saas.hp.com/l/28912/2015-07-21/32bhy3/28912/69168/IoT_Report.pdf. [Accessed: 6- Nov- 2015].
Hewlett Packard Enterprise Development LP, 'Find weak links in connected devices', 2015. [Online]. Available: http://go.saas.hp.com/l/28912/2015-07-21/32bhy7/28912/69172/IoT_Weak_Links_Brief.pdf. [Accessed: 6- Nov- 2015].
|
|
|
|
CSA Events and Activities
The latest updates about CSA APAC events and activities.
|
|
|
|
|
CSA Innovation Conference, 28-29 October, Singapore
The two day conference was successfully held on the 28th and the 29th of October in Suntec Singapore International Convention & Exhibition Centre, Singapore. On the first day of the conference, our speakers presented their experiences and thoughts on how innovation enhances their companies. CSA-STAR workshop and Crowdfunding 101 session were conducted on the second day, our audiences had the opportunities to understand more about STAR certification and Crowdfunding. Throughout the event, our exhibitors showcased their latest innovative products to the visitors at the CSA Innovation Pavillion.

|
|

|
|
|
|
|
|
CSA NCR Chapter
Featured chapter of the month

|
|
The Cloud Security Alliance, NCR Chapter(India) was co-founded by Prof. K. Subramanian ,Vipin Kumar Uboweja and Madhav Chablani, who is Chairman of CSA , NCR Chapter(India). This chapter is working for increasing CSA’s visibility with Government, Industry, Academia and other National Professional associations, with Focus on strengthening CSA’s Advocacy and Awareness, promotion and outreach ,by building on Strategic Partnerships and Alliances. Chapter is also working for Member’s Growth and Participation, by working towards Formation of Study Groups and increasing Certified members. Working on joint initiatives with CCICI(Cloud Computing Innovation council of India),for e-Gov reference architecture for cloud computing, NASSCOM(National Association of Software and Services Companies is a trade association of Indian Information Technology and Business Process Outsourcing industry and NPO) as member in Cyber Security Task Force and for mentoring Startup Community, NISG (National Institute of Smart Governance) on Government initiatives ,discussing CSA’s Innovation and Research with knowledge communities and addressing academia in Premiere Institution in India.
Cloud Computing India 2015, 3rd International Conference was held on the 6th of August, in Shangri-La’s Eros Hotel in New Delhi, India. Cloud Security Alliance was the Cloud Security Strategic Partner for this event. CSA APAC Managing Director, Aloysius Cheang, delivered a keynote speech on Top 5 Cloud Trends for 2015. The objective of this exclusive conference was to help the information and technology experts understand the potential business impacts of cloud computing now and in the future and to keep up-to-date with the trends and updates in the industry. It also gave professionals a chance to learn from the experience of those who are in the process of, and those who have already implemented cloud computing.
|
|
|
|
|
APAC Volunteer Leadership Spotlight
|
|
|
|
|
Mr. Madhav Chablani

|
|
Madhav Chablani is the Cloud Security Alliance, NCR Chapter(India), Founder and Chairman, passionately involved for CSA’s Advocacy, Promotion, Growth and Outreach. He is Working Group Member with CCICI(Cloud Computing Innovation council of India), a think tank formed by Government, Industry, academia and professional associations participation, representing CSA – for formulating "e-Gov Reference architecture for cloud computing" for India. He is also Cyber Security Task force member with NASSCOM, for concerns on National Cyber Security Capacity building, representing CSA, for recommendations on Cyber Security Skills, Policy and Product Innovations for India. He has remained active with ISACA HQ, was in External Advocacy Board and India Growth Task force. He is passionately involved in contributions with CSA’s Innovation and research and discussing with knowledge communities and addressed academia at IIT’s, IIIT and IIM’s, NASSCOM’s Startup community and stakeholders. He is professionally involved as Consulting CIO and mentoring Startup’s.
|
|
|
CSA APAC Events
- Inaugural CSA New Zealand Summit, 19 November, 2015, Wellington, New Zealand
- 3rd CSA APAC Congress and 6th CSA Greater China Summit,1-3 December, 2015, Guangzhou, China
Registration is open now! To register or for more event information: Click Here
|
|
|
Co-Editors for this Newsletter:
- Lynne Yang - Assistant Research Analyst
- Mobile: +65 9726 2846
- Email: [email protected]
- Mickey Law - Assistant Research Analyst
- Mobile: +64 21 049 3893
- Email: [email protected]
If you are interested in utilising the CSA Cloud Codebook for marketing purposes, please contact the co-editors.
|
|
| | |